2023 set many records. The fastest marathon, the world’s largest pizza, and even the most dogs in a conga line, to name a few. But among the many highlights, a darker record was set— an all-time high for data breaches, impacting more than 116 million individuals.
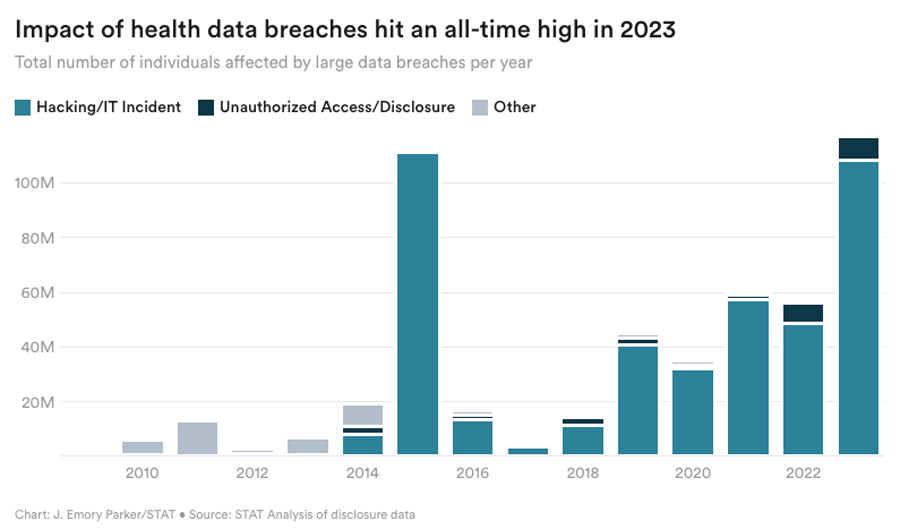
While this isn’t a record to celebrate, it’s a perfect time for us at Redox, as protectors of patient data, to share our best security advice with our current customers and the healthcare community.
Redox employs a comprehensive security program that exceeds industry standards to keep our customers and their data safe. We are all patients, so keeping this data safe is important to all of us.
To help you in this effort, we’ve compiled the most important security questions to ask when evaluating partners that will handle your protected health information (PHI), especially data integration, data analytics, or data hosting vendors.
1. Are you HITRUST certified? At what level?
A good way to ensure a company is doing what they say they are doing is to look at certifications. Certification from The Health Information Trust Alliance (HITRUST™) is a great way to do this, especially if you are asking the right questions. HITRUST delivers data protection standards and certification programs to help organizations safeguard sensitive information, manage information risk, and reach compliance goals. HITRUST created and maintains the Common Security Framework (CSF), a certifiable framework to help healthcare organizations and their providers demonstrate their security and compliance in a consistent and streamlined manner. It’s critical to ensure a vendor is actually HITRUST certified—not just using the logo—and validated at the appropriate level for your risk appetite.
There are significant differences between the levels of HITRUST certification. If you are sharing a significant amount of PHI (and risk) with a vendor, you should validate they are HITRUST certified at the r2 level. (At Redox, we are r2 certified, backed by an independent auditor.) With more than 1,800 validated controls, r2 is the most comprehensive level of all three HITRUST certifications. It also requires an ongoing assessment of these controls, not just a yearly audit. Based on more than 40 security frameworks, r2 is widely regarded as the HITRUST certification for those with the highest commitment to data security
2. What is your process for continuously evaluating your third-party vendors?
Third-party security breaches were frequent in 2023. With a growing number of point solutions, data integration, data analytics, or data hosting organizations may deploy many vendors to help solve issues without the necessary scrutiny. Even if they do a proper evaluation at purchase, they may quickly lose sight of the third-party vendors as the years go by without a process to continuously evaluate. This can lead to a large amount of risk being introduced that is not being tracked or managed.
At Redox, we are constantly looking for ways to improve and monitor our third-party vendors. All our vendors go through a complex evaluation process, conducted by multiple departments—not just security—before getting the green light for use. Our vendors are then evaluated on at least a yearly basis to ensure they are keeping up with their security requirements. Redox will not hesitate to replace a vendor if they increase the risk to our customer’s data.
3. How do you ensure security is built into your products?
When developing software that is at the heart of sensitive data protection, vendors often fail to fully utilize a Secure Software Defined Lifecycle framework. Security is brought in too late and software is released with fingers crossed that malicious attackers won’t find any vulnerabilities.
At Redox, security experts are included throughout the software development lifecycle. We consider security at the point of conception for each software release, not just on the back end after the development is complete. Before going live, we thoroughly vet and test software, tapping the expertise of outside parties. This brings us to the next question…
4. How do you continuously test your security safeguards?
Third-party PEN tests are great and required for HITRUST, but they rarely happen more than once a year, and they may not dive deeply into all areas of a product due to time constraints. Any vendors you’re considering should be able to explain how they are ensuring the safeguards the rest of the time.
Outside of third-party PEN tests, internal PEN tests, and tabletop exercises, Redox partners with HackerOne on a public-facing bug bounty program. While we do 24/7 active threat hunting and monitoring, the bug bounty program incentivizes security researchers to find security vulnerabilities that we may have missed. Every new Redox feature is scrutinized by both our internal experts and these researchers before it is released.
5. Are you fully cloud-hosted?
Cloud providers keep the underlying infrastructure secure and up-to-date, which can remove a lot of security complexity. Vendors that are fully cloud-hosted have no physical data centers to worry about or physical infrastructure to manage; this also means they can employ a more focused staff specialized in cloud security. On-premise, or hybrid, applications require the application vendor’s team (and yours) to have additional security knowledge and expertise. Additional risks are also brought on by having to worry about the underlying hardware and networking.
Redox is fully cloud-hosted on either AWS or Google Cloud. This means we can be hyper-focused on securing one type of infrastructure, allowing us to move at a greater speed by taking advantage of the latest security advances offered by our cloud partners.
6. Do you employ 24/7/365 monitoring for customer accounts?
If you are sharing data risk with a vendor, you should ensure they are actively monitoring for compromised accounts—not just their own accounts, but also your accounts created on their systems. Most vendors will tell you this isn’t their problem, but when healthcare data is at play it’s really everyone’s problem.
Redox monitors all customer accounts 24/7/365, and not just your typical Dark Web scans. In the past year, we have helped several customers identify compromised accounts. In each case, we detected the compromise in less than 24 hours, took action to remove the credentials from malicious marketplaces, and contacted the customer to work and triage the incident.
The answers to these questions will set you on a path to peace of mind and reduced risk. You can spend less time worrying about the security of your data and devote more time to all the other important work you have to do, which may or may not involve canines and conga lines.
Click if you’d like to learn more about Redox’s security measures and protocols.

